What Are Identity Theft and Identity Fraud. The identity theft insurance benefit for members is underwritten and administered by any one of the following insurance carriers depending upon your program.

Pdf Identity Theft Identity Fraud And Or Identity Related Crime
Threats to a users safety or privacy.

. Forensic investigations are specialist in nature and the work requires detailed knowledge of fraud investigation techniques and the legal framework. Identifying the type of. Code of Conduct.
LMP can now directly assists with your investigation process. Coverage is provided under a master group policy issued in the name of Sontiq Inc. PEACE Model of Investigation Interviews.
AIG Assurant or Hamilton Insurance DAC andor its affiliates. This includes critical peace officer jailer 911 telecommunications and security e-commerce training. OSS Academy provides quality online law enforcement corrections and telecommunications training courses.
The Payment Card Industry Data Security Standard PCI DSS is the data security standard created to help financial institutions process. Upon completion of the investigation if it is found that you were a true victim of identity theft a revised 1099G will be issued to you. Look for the purple CE Eligible tags to see which webinars.
Review FTC wwwidentitytheftgov information for additional steps to recover from identity theft. We are dedicated to the privacy and safety of every Xbox Live member and cannot tolerate any attempts to steal accounts or personal information. If a data breach happens you must tell any users whose personal data might have been affected.
The FTC also offers guidance to businesses on how to inform employees of the incident and additional steps businesses may take. LI also investigates tips from the public. You must pass an identity.
Identity theft and identity fraud are terms used to refer to all types of crime in which someone wrongfully obtains and uses another persons personal data in some way that involves fraud or deception typically for economic gain. The purpose may be to obtain goods or services or to make payment to another account which is controlled by a criminal. If you want to request an IP PIN please note.
Analytic techniques are an important addition to every analysts toolbox. A single message directing your friends to a phishing website can lead to many stolen accounts. If you are a confirmed victim of tax-related identity theft and we have resolved your tax account issues well mail you a CP01A Notice with your new IP PIN each year.
The National Sex Offender Public Website enables every citizen to search the latest information from all 50 states DC Puerto Rico Guam and Indian tribes for the identity and location of. PLANNING THE INVESTIGATION The investigating team must carefully consider what they have been asked to achieve and plan their work accordingly. A summary of the terms of coverage are.
Defender for Identity security alert evidence lists provide the related entities that are involved in each potential lateral movement path. What Are The Most Common Ways That Identity Theft or Fraud Can Happen to You. For the benefit of members.
Images and recordings including photographs video and audio records which are part of inactive investigative files and which are clearly offensive to common sensibilities are. File a complaint with the Federal Trade Commission the lead federal agency on identity theft issues. Learn investigation strategies from industry experts Webinars.
The Crime and Intelligence Analysis option trains graduates to successfully apply the tools and techniques required for solving complex investigations. Computer technology is the major integral part of everyday human life and it is growing rapidly as are computer crimes such as financial fraud unauthorized intrusion identity theft and intellectual theft. Criminal activity can relate to road use such as speeding drunk driving or to matters such as theft drug distribution assault fraud etc.
The objectives of the investigation will include. To counteract those computer-related crimes Computer Forensics plays a very important role. Emotional or financial damage to a user.
If you dont already have an IP PIN you may get an IP PIN as a proactive step to protect yourself from tax-related identity theft. Computer Forensics involves obtaining and analysing digital. We source expert presenters for our webinars and provide certificates for continuing education CE credits.
The evidence lists directly help your security response team increase or reduce the importance of the security alert andor investigation of the related entities. Inactive investigative data are public unless the release of the data would jeopardize another ongoing investigation or would reveal the identity of individuals protected under subdivision 17. Our adult based learning programs are interactive and are in use by numerous professional public safety entities.
As criminals become more proficient analysts must be able to use equally sophisticated analytical skills. Credit card fraud is an inclusive term for fraud committed using a payment card such as a credit card or debit card. When the police have concluded their investigation a decision on whether to charge somebody with a criminal offense will often be made by prosecuting.
Phishing typically leads to financial loss identity theft a violation of personal privacy and other avenues of fraud outside of Xbox Live. What are the penalties for. It provides students with the critical thinking skills.
The investigation of criminal activity is conducted by the police. The department uses a variety of techniques to uncover fraud including cross-matching records with the Social Security Administration and the state and federal lists of new hires.

Calameo Identity Theft Protect Your Identity Online

Tips And Advice To Prevent Identity Theft Happening To You Europol

Pdf Online Id Theft Techniques Investigation And Response
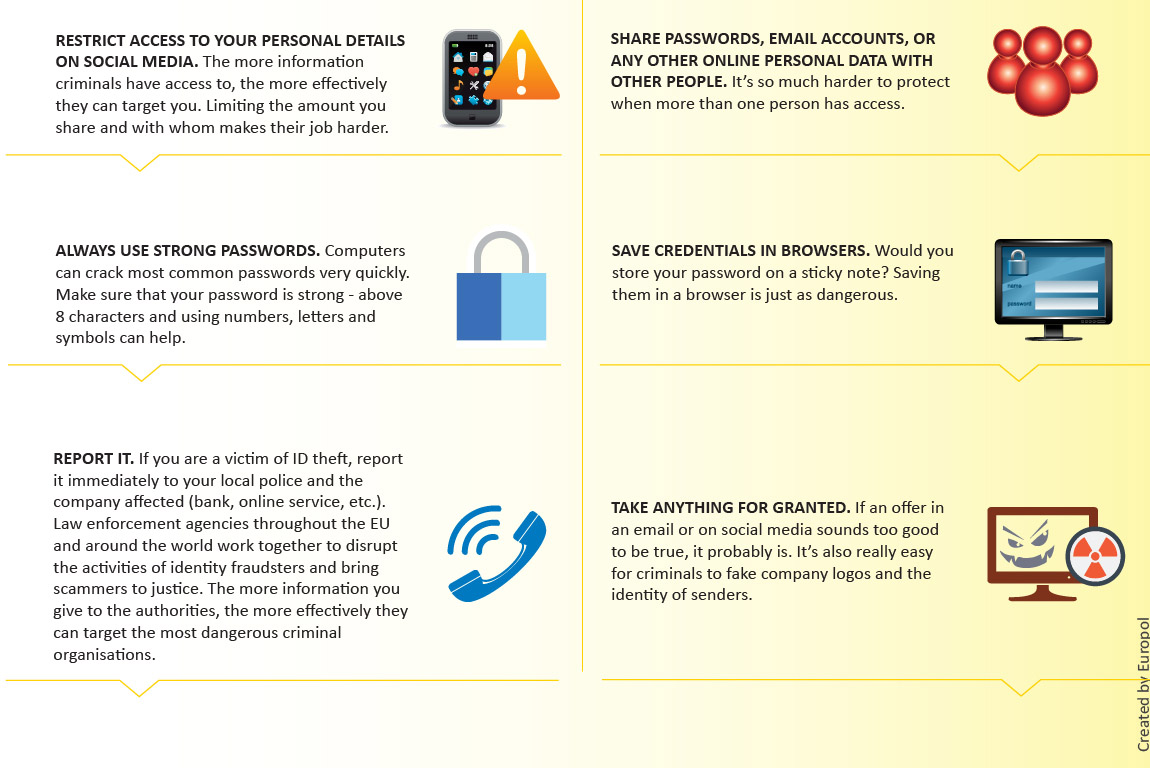
Tips And Advice To Prevent Identity Theft Happening To You Europol



0 comments
Post a Comment